Have you noticed that many Modern Enterprises are transitioning to Cloud-Based environments?
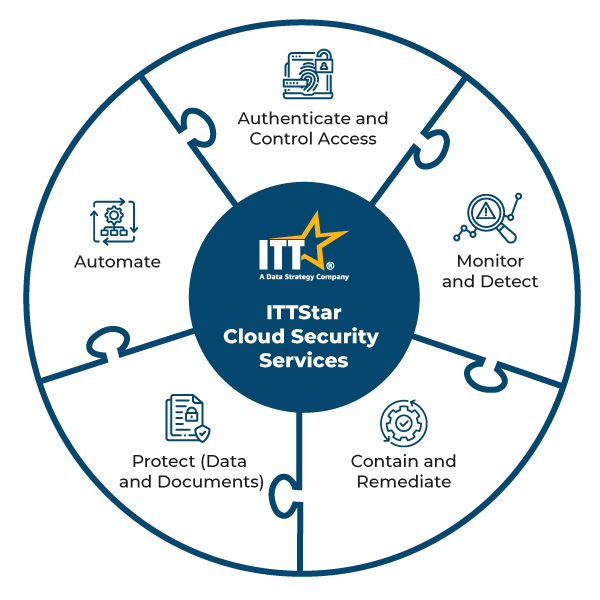
Whether your organization operates in a public, private, or hybrid cloud environment it is essential to make cloud security a priority, regardless of the size of your enterprise. At ITTStar, we believe in a robust cybersecurity framework to mitigate the risks associated with cloud security. Our approach is centered around five key pillars: Identify, Protect, Detect, Respond, and Recover. By identifying potential threats, implementing strong cloud application security measures, detecting breaches in real time, responding quickly, and recovering effectively, we can ensure that your cloud infrastructure always remains secure.
Cloud Security Services
Identifying Potential Threats
In the ever-evolving threat landscape, proactive identification of potential vulnerabilities is the first line of defense. Our team of experts at ITTStar stays vigilant, conducting thorough assessments and audits to pinpoint any weak spots in your cloud infrastructure. By adopting a comprehensive risk management approach, we help you understand the specific threats your enterprise may face.
Implementing Strong Protection Measures
Once potential threats are identified, it's crucial to fortify your cloud environment with robust protection measures. ITTStar works closely with your organization to design and implement stringent security controls, ensuring that your sensitive data and critical applications are shielded from unauthorized access, data breaches, and cyberattacks. From encryption and access management to multi-factor authentication, we deploy cutting-edge security technologies tailored to your specific cloud environment.
Real-Time Breach Detection
Despite the most robust security measures, breaches can occur. Rapidly detecting and responding to such incidents is crucial to minimizing the impact. ITTStar leverages advanced threat detection mechanisms and state-of-the-art monitoring tools to provide real-time visibility into your cloud infrastructure. By continuously analyzing logs, network traffic, and user behaviour patterns, we swiftly identify any anomalies or suspicious activities, enabling proactive incident response.
Quick and Efficient Incident Response
In the event of a security incident, a prompt and efficient response is vital to mitigate further damage. Our skilled incident response team at ITTStar is well-versed in handling cloud security incidents. We follow industry best practices and work closely with your organization to contain the breach, investigate its root cause, and implement necessary remediation measures. Our goal is to minimize downtime, protect your assets, and restore normal operations swiftly.
Effective Recovery Strategies
In the face of a cloud security incident, the ability to recover effectively is crucial to ensure business continuity. ITTStar helps you develop comprehensive recovery strategies, including data backup and disaster recovery plans. By leveraging the latest cloud technologies, we facilitate seamless recovery, enabling you to bounce back quickly and efficiently.