Security Operations Center
Your Security, Our Promise
Introducing ITTStar - a world class and affordable provider of SOC as a service.
Our managed SOC services give round-the-clock protection for all your digital assets. Our SOC team consists of industry experts with access to the latest technology and cybersecurity know-how. These resources allow us to cater to all your security requirements, including:
- Surveillance
- Threat detection
- Quick incident response
- Regulatory compliance
SOC by ITTStar – the protection your business needs!
Drop your Details, We’ll Contact you.
Why Your Business Needs Our SOC
Modern Threats Demand Modern Defenses
Cybercrimes are rampant around us. Managed SOC providers are a dime a dozen, but often not cheap to hire. Your business deserves the best-in-class protection without burning through your finances.
Manual defenses alone can no longer keep up with modern threats. Your cloud-native environments, hybrid infrastructures, and remote teams need advanced defense mechanisms.
That’s why we integrate our SOC infrastructure with everything from automated threat detection to 24/7 dedicated surveillance. We design our SOC for the modern enterprise – scalable, secure, and future-ready!
Tools We Use
Splunk
Real-time log analysis tool that collects, correlates, and visualizes security data across systems to detect and investigate threats.
Splunk on- call

Incident response platform that routes alerts to the right teams instantly, improving response time and reducing downtime.
Crowdstrike

Endpoint protection tool that detects malware, ransomware, and suspicious behavior on devices in real time.
Zscaler

Cloud-based security platform that secures internet access and monitors user activity to prevent data leaks and cyber threats.
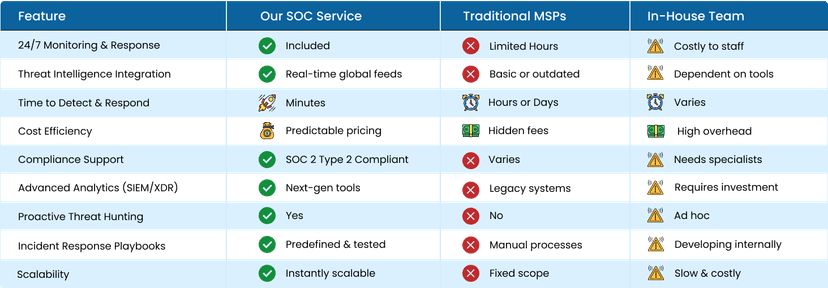
Feature Comparison
SOC Solutions for Industry Challenges
AI/GenAI Solutions
AI-driven PMS that improves diagnostic accuracy, efficiency, and patient care.
What We Implement:

Why Choose Us
As our client, you get access to all our exclusive services, including
%2B1.png&w=256&q=75)
Assessment
A thorough SOC assessment to evaluate your security framework

Smart Automation
Integrated AI and cloud services that automates the routine, repetitive tasks in your security operations
Did We Mention We Are SOC 2 Type 2 Compliant?

Yes, that’s right! Our SOC 2 Type 2 compliance will keep your business security audit ready – anytime, anywhere! With our support, you can face your SOC 2 audit like a champion!

Personalized Services
SOC services that are personalized to remedy the weaknesses in your framework

Real-Time Intelligence
Track all events and receive instant security notifications with intuitive dashboards.
Our Partners

.png&w=828&q=75)




.png&w=828&q=75)


Insights
Case Studies
What Clients Say About ITTStar

Frequently Asked Questions


.jpg&w=828&q=75)
.jpg&w=828&q=75)
.jpg&w=828&q=75)
.png&w=828&q=75)












.png&w=640&q=75)
.png&w=640&q=75)